HITRUST CSF
Control Threat Analysis
Cyber Threat Adaptive Update
HITRUST uses a comprehensive and continuous process to identify threats, align mitigations that counter ongoing and new threats, and position the organization to respond effectively. The HITRUST CSF is regularly reviewed and updated as necessary to respond to the constantly shifting threat landscape through this process.

Static security programs can't keep up.
HITRUST's Cyber Threat Adaptive program can.
Cyber threats evolve rapidly, static or slow-moving security frameworks and programs built around higher-level security objectives struggle to remain effective. Attackers move faster than ever, exploiting gaps and weaknesses before organizations can react. The result? Security controls that look good on paper but fail to respond a changing threat landscape.
At HITRUST, we’ve tackled this challenge head-on with our Cyber Threat Adaptive (CTA) program. This innovative solution stress-tests the HITRUST framework with real-world threat intelligence, ensuring our controls remain highly relevant and effective against emerging risks and support the organization’s ongoing compliance obligations.
Our report details findings covering the period from 7/01/2025 to 12/31/2025. Our research confirms that our i1, e1, and r2 requirement selections are responsive to the current threat landscape. During this period, we analyzed 588,588 threat indicators compiled from 4,650 threat-intelligence articles were analyzed and mapped to 46,175 MITRE ATT&CK technique and mitigation pairs. The most commonly observed attack techniques, including phishing, drive-by compromise, and exploitation of public-facing applications, remained well mitigated by controls already embedded in the HITRUST e1, i1, and r2 assessments.
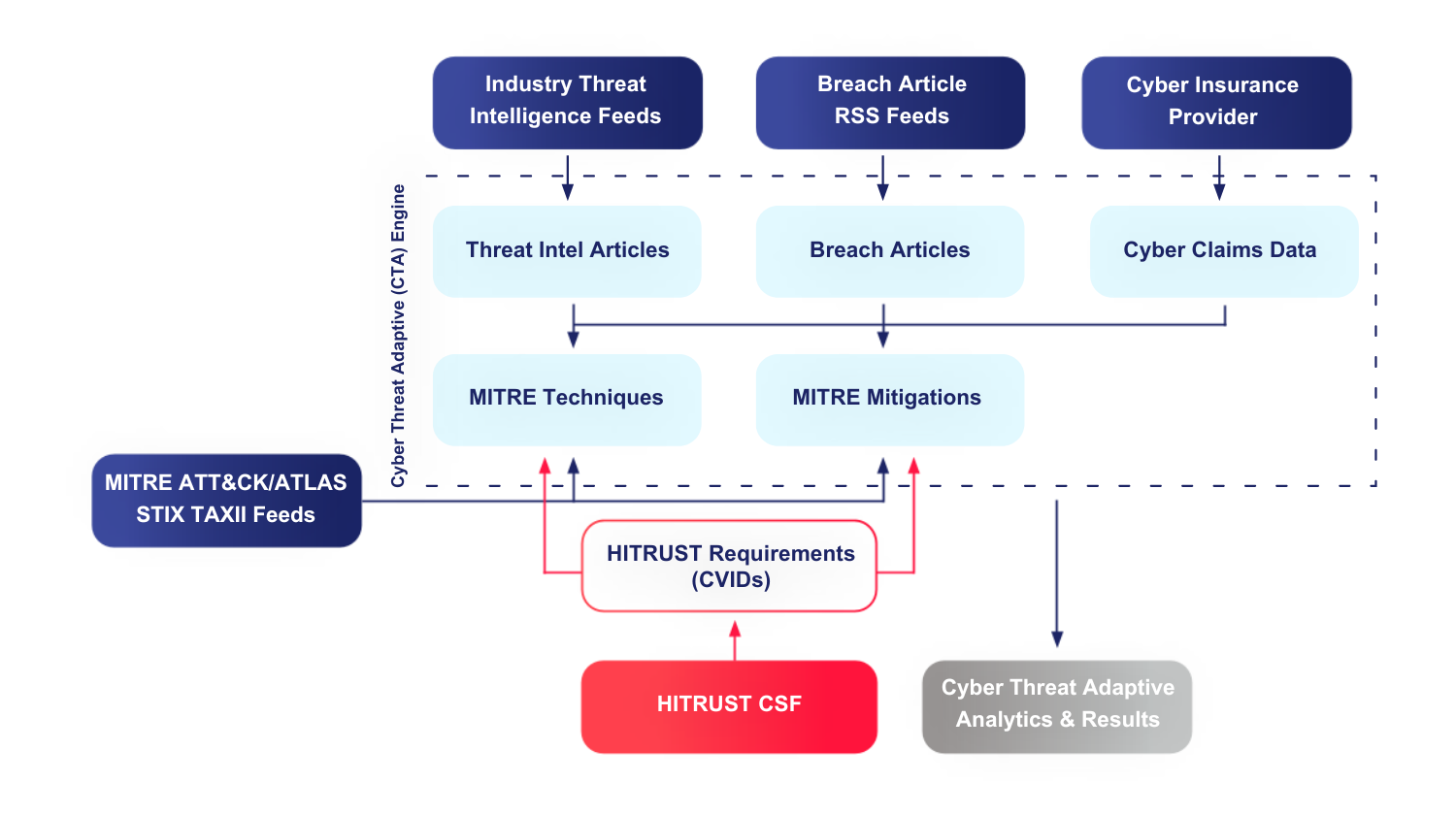
How it Works
HITRUST CSF Control Threat Analysis
View CSF Control Threat Analysis Reports, offering detailed insights into the evolving threat landscape and the rationale behind control requirements. These reports help organizations understand how emerging risks, industry trends, and threat intelligence shape the HITRUST CSF framework—supporting stronger, risk-based security and compliance strategies.