Implementation and Timeline
The ability to perform HITRUST Implemented 1-Year (i1) assessments in MyCSF will be released at the start of the 2022 calendar year. The updates to the Risk-based, 2-Year (r2) assessment (formerly the HITRUST CSF Validated Assessment) reports described in this advisory will be reflected in all r2 reports issued 12/31/21 and later.
Overview
To date, HITRUST has offered only one information protection certification, the HITRUST CSF Certification, achievable only by demonstrating sufficiently strong control maturity through the performance of a validated assessment. By design, this single HITRUST certification offers a gold standard level of assurance due to the comprehensive control requirements and assurance program requirements. However, completion of a HITRUST validated assessment can be a significant undertaking for an organization. HITRUST acknowledges that the highest level of information protection assurance is not needed by every organization or vendor relationship.
A broader range of certification options is necessary to address varying assurance requirements and needs—as determined by factors such as level of effort, budget, and purpose. To address these needs, HITRUST is introducing the HITRUST Implemented, 1-year (i1) Certification, a new assessment mechanism and accompanying certification that requires reduced effort and cost than today’s validated assessment, while still living up to the gold standard level of quality for which HITRUST certifications are known. To differentiate the certifications in our newly expanded assessment portfolio, HITRUST is also renaming our existing certification to the HITRUST Risk-based, 2-year (r2) Certification. Further, HITRUST is taking this opportunity to update the content, layout, and formatting of HITRUST-issued certification reports.
The HITRUST Risk-based, 2-year r2 Certification will continue to provide the highest level of information protection assurance for situations with greater risk exposure due to data volumes, regulatory compliance, or other risk factors. The new HITRUST Implemented, 1-year i1 Certification will provide, when compared to the r2, a relatively moderate level of information protection assurance, focusing on good security hygiene and cybersecurity best practices controls. Both the i1 and r2 certifications will uphold the high-quality bar for which HITRUST is known.
Key similarities between i1 and r2 certifications
The HITRUST Implemented, 1-year i1 Certification shares several characteristics with the HITRUST Risk-based, 2-year r2 Certification, the most notable of which include:
- Both provide a means to convey information assurances over the assessed entity’s scoped control environment through a shareable, final report with certification issued by HITRUST.
- Both use requirements resident in the HITRUST CSF and use MyCSF.
- Readiness assessments and validated assessments can be performed for both.
- Both require an Authorized HITRUST External Assessor Organization to inspect documented evidence to validate control implementation.
- Both leverage the HITRUST Control Maturity Scoring Rubric (although the i1 does not use the entire rubric). While the rubric has been updated in support of the i1 assessment (as described in HAA 2021-013), no significant changes were made to the rubric to accommodate its use on i1 assessments other than indicating that only the Implemented control maturity level is considered during i1 assessments.
- Final reports resulting from i1 assessments (such as the HITRUST i1 Validated Assessment Report) can be shared through the HITRUST Assessment XChange just like those resulting from r2 assessments, and i1 assessment results can be shared through the HITRUST Results Distribution System just like the results of r2 assessments.
- The external assessor’s fieldwork window is capped at a maximum of 90 days on both i1 and r2 assessments.
Key differences between i1 and r2 certifications
The i1 and r2 are distinct in many ways, the most notable of which are:
- r2 certifications are valid for 2 years, while i1 certifications are valid for 1 year.
- While the HITRUST CSF requirements considered in r2 assessments are tailored based on the assessed entity’s inherent risk factors (such as whether in-scope systems are accessible from the Internet, whether wireless networks are used in the scoped environment, etc.), the HITRUST CSF requirements in an i1 assessment are carefully curated by HITRUST and only vary when performed against different versions of the HITRUST CSF.
- r2 assessments can be tailored to optionally convey assurances over dozens of information protection regulations and standards (including HIPAA, NIST CSF, PCI DSS) while i1 assessment are pre-set.
- While r2 assessments can be tailored to include all security control references present in the HITRUST CSF through use of the “comprehensive assessment” option, i1 assessments cannot.
- Privacy-centric HITRUST CSF controls and requirements can optionally be added into an r2, but not into an i1. While certain requirements within domain 19 are included in i1 assessments, the i1 is designed to focus on cybersecurity only.
- Many control maturity levels (policy, process, implemented, and optionally measured and managed) are considered when scoring HITRUST CSF requirements included in r2 assessments, while the scoring of HITRUST CSF requirements included in i1 assessments considers only control implementation. In other words: only control implementation is considered during i1 assessments.
- HITRUST CSF requirements performed by the assessed entity’s service providers (such as cloud service providers) on behalf of the organization can be carved out / excluded from consideration in i1 validated assessments, but such carve-outs are not permitted in r2 assessments.
- Interim assessments are not necessary for i1 certifications, as a full re-assessment is necessary each year to maintain i1 certification status.
- r2 certifications can be bridged through a HITRUST Bridge Certificate, while i1 certifications cannot.
- Validated r2 assessments can result in a HITRUST-issued certification over the NIST Cybersecurity Framework, while i1 validated assessments cannot.
- Newly created i1 assessments must use the most current version of the CSF available at time of object creation.
- Minor differences are present on the External Assessor QA checklist used on i1 assessments, as certain checklist items are only applicable on r2 assessments.
More information about the i1 certification and i1 assessments
HITRUST’s quality assurance (“QA”) review of i1 assessments
i1 assessments will feature the same high quality of deliverables as r2 assessments, as ensured through HITRUST’s robust Quality Assurance process, which includes the HITRUST Assurance Intelligence Engine. In addition, just like on r2 assessments, HITRUST’s QA review of i1 assessments must be scheduled using the HITRUST QA Reservation System. Please be aware that i1 and r2 assessments require different types of report credits to book a reservation. For additional information on acquiring the correct type of report credit please contact your Customer Success Manager (CSM).
HITRUST will perform a sample-based QA review for i1 validated assessment submissions much in the same manner as is performed on r2 validated assessment submissions. The notable difference is that HITRUST will not QA a sample of requirements with measured and/or managed scores on i1 submissions in addition to reviewing a “Core QA” sample of requirements (as i1 assessments do not consider the measured and managed control maturity levels).
The time necessary to perform a quality assurance review of any validated assessment submission varies based on the complexity of the assessment, on the quality of the external assessor’s documentation, the quality and consistency of the external assessor’s validation procedures, and on many other factors. However: HITRUST’s established i1 post-submission Service Level Agreement (SLA) is not greater than 45 business days with HITRUST (otherwise the customer’s next i1 validated assessment report credit is complimentary). This Service Level Agreement (SLA) is calculated using a measurement called “days with HITRUST.” The measurement is calculated from the earlier of the day that HITRUST begins QA (the day the assessment moves into the Performing QA phase) or the last day of the QA block from the reservation. Days are counted for any business days where the assessment is in a HITRUST owned phase before the draft report is posted. Validated assessment submissions entering escalated QA due to quality concerns are exempted from this SLA, as processing such submissions may take longer than processing non-escalated submissions. The days with HITRUST measure are visible to customers as part of the assessment details page within MyCSF. Should HITRUST exceed the stated SLA, customers can request a complimentary report credit by contacting their Customer Success Manager within 14 days after the final report has been issued.
Usability improvements on i1 assessments
Those performing i1 assessments will enjoy several usability and quality-of-life enhancements in MyCSF, including:
- All i1 assessments feature HITRUST’s enhanced Assessment Workflows, webforms, and Kanban-style status tracking boards. For additional details, see all HITRUST Advisories or you can see more information for these specific advisories.
- Illustrative procedures of HITRUST CSF requirements for versions 9.6 and later feature formatting and list items to aid in easily identifying the illustrative procedure’s unique content. In i1 assessments, this illustrative procedure enhancement applies only to the implemented level (as only the implemented control maturity level is considered in i1 assessments). In r2 assessments, this illustrative procedure enhancement applies to both the policy and implemented levels. Pictured below is an example of an implemented illustrative procedure featuring this enhancement:
Figure 1 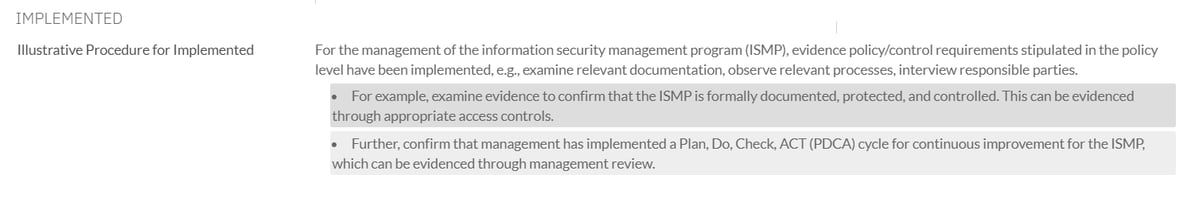
- On i1 assessments, the unique elements associated with each HITRUST CSF requirement which must be implemented by the assessed entity and evaluated by the External Assessor (referred to as “evaluative elements”) are not shown in the requirement’s policy illustrative procedure (as they are in r2 assessments), because i1 assessments do not consider the policy control maturity level. Instead, i1 assessments present each HITRUST CSF requirement’s evaluative elements as stand-alone sentences in a numbered list. Further, the count of evaluative elements associated with each HITRUST CSF requirement is clearly shown in MyCSF for i1 and r2 assessments using HITRUST CSF v9.6 and later. An example of the new “Evaluative Elements” count is pictured below as well as an example of enumerated and numbered evaluative elements.
Figure 2

Figure 3

- In i1 and r2 assessments using HITRUST CSF v9.6 and later, a new sampling badge is shown in MyCSF for each HITRUST CSF requirement having an implemented illustrative procedure that calls for testing a sample. This sampling badge helps external assessors quickly and easily identify areas where sampling may be required during the testing of the implemented control maturity level. When this sampling badge is present, the external assessor is expected to perform sample-based testing. If circumstances exist which prevent sample-based testing (such as a lack of control occurrences), the external assessor must document a rationale (in the test plan and/or in external assessor comment fields in MyCSF) for not performing sample-based testing for that HITRUST CSF requirement’s implemented control maturity level. Pictured below is an example of this sampling badge and accompanying mouse-over tooltip. An indicator is present in the new, downloadable test plan template (discussed below) showing the requirements possessing this sampling badge.
Figure 4 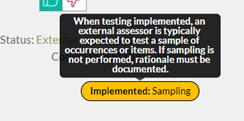
- A new, Excel-based test workbook template will be available for use by assessors performing i1 assessments. This template can be downloaded from the test plan upload page in MyCSF. External assessors are not required to use this test plan template.
- Assessed entities and their external assessors have flexibility with respect to who populates an i1 assessment in MyCSF. Personnel from either the assessed entity or their external assessors are allowed to enter control maturity scoring and assessment scoping information in i1 assessments. When a member of the external assessor enters control maturity scoring and/or assessment scoping information, MyCSF will automatically apply the external assessor’s thumbs-up / agreement. However, when control maturity scoring and/or assessment scoping information is initially entered by the assessed entity, a member of the external assessor team is required to evaluate the entered data and manually enter their thumbs-up / agreement. This added flexibility allows control maturity scoring and assessment scoping information to be either (a) initially populated in MyCSF by the assessed entity and then manually agreed to by the external assessor (just like in r2 assessments), and/or (b) populated and auto-agreed entirely by the external assessor. There is no preference or option to configure; MyCSF will recognize the role (external assessor, standard user) and adjust accordingly. As a result of this added flexibility and to reflect that submission of a completely and accurately populated MyCSF assessment to HITRUST is ultimately the External Assessor’s responsibility, an i1 validated assessment’s not-yet-scored requirements are shown in the Kanban-style status view as pending the External Assessor team.
HITRUST CSF requirements included in i1 assessments
HITRUST CSF requirements are included in r2 assessments through the combination of a purposive sample of 75 HITRUST CSF control references required for certification, the inherent risks present in the assessed environment (such as whether the scoped system is accessible from the Internet), and the optional inclusion of regulations and standards such as PCI DSS, HIPAA, and EU GDPR. As a result, the HITRUST CSF requirements included in r2 assessments can vary from as few as 198 requirements to nearly 2000 requirements.
A completely different approach drives the selection of HITRUST CSF requirements included in i1 assessments. HITRUST has carefully selected the HITRUST CSF v9.6 requirements to be included in i1 assessments in light of several factors:
- The i1 is designed to be an industry-agnostic assessment, so the HITRUST CSF requirements included in the i1 assessment and their associated illustrative procedures and evaluative elements are also industry-agnostic and do not use any terminology specific to the US federal government or germane to any specific legislation or authoritative source (e.g. does not include terms such as “protected health information”, “cardholder data”, or “authority to operate”).
- The i1 is designed to be an evolving, threat-adaptive certification that leverages threat intelligence and best practice controls to deliver an assessment that addresses relevant practices and active cyber threats. HITRUST evaluated existing information security controls to identify those relevant to mitigating known risks and leveraged cyber threat intelligence data from a leading threat intelligence provider spanning May 2021 to Oct. 2021 to influence the selection of technically focused HITRUST CSF requirements included in i1 assessments. As a result, the i1 includes controls that were selected exclusively to address emerging cyber threats actively being targeted today. HITRUST will review cyber threat intelligence data for potential updates to the i1 requirements on a quarterly basis to maintain the threat responsive nature of the i1. Updates to the i1 requirement statement selection will be published as part of either a major or minor release of the HITRUST CSF. Consequently, all i1 assessments performed against a particular version of the HITRUST CSF will include the same requirement statements.
- The i1 is designed to be a combination of good security hygiene controls and cybersecurity best-practice controls. The design affords a high degree of coverage against authoritative sources generally viewed as security best practices. As a result, the HITRUST CSF requirements included in i1 assessments provide a high degree of coverage against sources such as the HIPAA Security Rule; NIST SP 800-171; the NAIC Data Security Law; the FTC’s GLBA Safeguards Rule (both the current version as well as the 2021 proposed update); NISTIR 7621: Small Business Information Security Fundamentals; the DOL’s EBSA Cybersecurity Program Best Practices; and the HITRUST CSF requirements included in HITRUST’s Basic, Current-state (“bC”) assessment.
- All HITRUST CSF assessment domains and CSF control categories are represented in the i1.
Because the i1 consists of a selection of HITRUST CSF requirement statements, and because HITRUST CSF requirement statements are not included in the free HITRUST CSF PDF download, organizations interested in seeing the HITRUST CSF requirements included in an i1 assessment are encouraged to create an i1 assessment in MyCSF.
CAPs, scoring, and certification thresholds on i1 assessments
The scoring and certification thresholds for i1 assessments are different than those for r2 assessments, as follows:
- i1 assessment scoring will always be shown as the overall score (e.g., 75, 100) rather than the maturity rating (e.g., 1-, 3+). Because i1 assessments do not include all control maturity levels (and instead focus solely on control implementation), the control maturity rating scheme used on r2 assessments are not suitable for use on i1 assessments. Instead, only scores between 0 and 100 are used on i1 assessments.
- For an i1 validated assessment to result in certification, no assessment domain’s straight-average score can be below 83. (To contrast this scoring against r2 assessments: For an r2 validated assessment to result in an r2 certification, no assessment domain’s straight-average score can be below 62.)
- For i1 assessments, assessed entities are required to define Corrective Action Plans (CAPs) for all HITRUST CSF requirements meeting the following criteria: the requirement’s implemented maturity level scores less than “fully compliant” / 100 and the associated control reference (e.g., 00.a) averages less than 80. For any requirements where the implemented maturity level scores less than “fully compliant” / 100 and the associated control reference (e.g., 00.a) averages 80 or more, a gap is identified instead of a CAP. The difference between a gap and a CAP on an i1 assessment is that management of the assessed entity is required to provide a written plan of action for remediation of CAPs, but not for gaps.
External inheritance on i1 assessments
External assessors and assessed entities of i1 assessments will have two options to address situations in which a HITRUST CSF requirement is fully or partially performed by a service provider (such as by a cloud service provider):
- The Inclusive method, whereby HITRUST CSF requirements performed by the service provider are included within the scope of the HITRUST assessment and addressed through full or partial inheritance, reliance on third-party assurance reports, and/or direct testing.
- The Exclusive (or Carve-out), method, whereby HITRUST CSF requirements performed by the service provider are excluded from the scope of the HITRUST CSF assessment and marked as N/A with supporting commentary that specifies that the HITRUST CSF requirement is fully performed by a party other than the assessed entity (for fully outsourced controls) or through commentary describing the excluded partial performance of the control (for partially outsourced controls).
HITRUST has always and will continue to require that the inclusive method be used on all r2 assessments, but HITRUST will allow use of both the inclusive and exclusive methods on i1 assessments. Regardless of the assessment type or the approach utilized, the external assessor and/or assessed entity will be required to specify which method is utilized for each service provider relevant to the scope of an i1 assessment. Within the assessment object in MyCSF, the assessed entity and/or the external assessor is required to select Included or Excluded from a “Consideration in this Assessment” drop-down menu within the “Services Outsourced for In-Scope Platforms and Facilities” table on the “Scope of the Assessment” screen. (This value is locked to “Included” for all identified service providers relevant to the scope of r2 assessments.) This selected method will then be reflected in the final reports resulting from both r2 and i1 assessments.
Both approaches may be utilized in the same i1 assessment (e.g., using the inclusive approach on one service provider and the exclusive approach on another). Applying both the inclusive and carve-out methods for the same service provider is not permitted, and therefore only one method can be selected for each service provider relevant to the scope of the assessed entity’s assessment. In instances in which a requirement is partially performed by the assessed entity and partially performed by a carved-out service provider, the assessed entity’s and/or external assessor’s commentary must clearly reflect that the requirement’s control maturity scoring is reflective of just the requirement’s performance by the assessed entity.
When the Inclusive method is utilized on i1 assessments, the same options are available for using the work of others as exist on r2 assessments:
- Inheritance of results or reliance upon another validated HITRUST CSF assessment,
- Reliance on audits and/or assessments performed by a third party, and/or
- Reliance on testing performed by the assessed entity (i.e., by internal assessors).
When inheritance or reliance methods are utilized to address requirements performed by a service provider, that service provider must be marked as Included within the “Services Outsourced for In-Scope Platforms and Facilities” table on the “Scope of the Assessment” screen within MyCSF.
Cross-assessment-type inheritance is allowed, meaning that an r2 assessment’s results can be inherited into an i1 assessment (and vice versa). However, only the implemented level’s scoring can be inherited when inheriting from an i1 assessment into an r2 assessment given that i1 assessments only consider the implemented maturity level. This limitation does not absolve those involved in the inheriting r2 assessment from either (a) accurately scoring the policy, procedure, and optionally measured and managed levels based on supplemental validation procedures or (b) scoring the policy, procedure, measured and managed scores at 0 to reflect the inability to ascertain scoring on these control maturity levels.
While HITRUST anticipates that most organizations who publish their HITRUST assessments for external inheritance will use r2 assessments instead of i1 assessments, service providers such as Cloud Service Providers (CSPs) do have the option to only perform and publish i1 assessments. In this case, their customers/tenants inheriting from them will be limited to inheriting only the implemented scoring and commentary (no policy, procedure, measured, or managed scoring will be available for inheritance).
Changes to HITRUST CSF reports
In addition to introducing the HITRUST Implemented, 1-year i1 Certification, HITRUST is applying layout and formatting updates to the HITRUST Risk-based, 2-year r2 Certification reports, as follows:
Changes to r2 reports
|
Reports Section* |
Changes** |
|
Cover page |
Additional graphics added |
|
1. HITRUST Background |
No Changes |
|
2. Letter of Certification or Letter of Validation |
No Changes |
|
3. Representation Letter from Management |
Minor wording changes to clarify the contents of the Management Representation Letter |
|
4. Assessment Context |
No Changes |
|
5. Scope of the Assessment |
No Changes |
|
6. Procedures Performed by the External Assessor |
No Changes |
|
7. Assessment Results |
|
|
8. PRISMA Control Maturity Model Overview |
|
|
9. Controls by Assessment Domain |
Section title changed to 9. Results by Assessment Domain to better describe the contents of the section. |
|
Appendix A – Corrective Action Plans Required for Certification |
No Changes |
|
Appendix B – Additional Gaps Identified |
Introductory paragraph added to describe the Additional Gaps table. |
|
Appendix C – Assessment Results |
No Changes |
*As defined in HITRUST Assurance Advisory 2021-011: HITRUST MyCSF Enhancements – HITRUST CSF Report Format Changes.
**Various sections noted above may include minor wording changes in order to differentiate between the HITRUST Risk-based, 2-year r2 Validated Assessment and the HITRUST Implemented, 1-year i1 Validated Assessment.
Differences between i1 and r2 reports
|
r2 Reports Section* |
Key Differences in an i1 Report |
|
Cover page |
No Differences |
|
1. HITRUST Background |
No Differences |
|
2. Letter of Certification or Letter of Validation |
Language amended to indicate the following:
|
|
3. Representation Letter from Management |
No Differences |
|
4. Assessment Context |
HITRUST i1 Validated Assessments do not leverage the scoping factors that are utilized for HITRUST r2 Validated Assessments. For that reason, rather than an outline of the r2 scoping factors, Section 4 of a HITRUST i1 Report will describe the i1 Validated Assessment, the level of assurances provided relative to r2 assessments, and the approach used to select the HITRUST CSF requirements included in i1 assessments. |
|
5. Scope of the Assessment |
No Differences |
|
6. Procedures Performed by the External Assessor |
|
|
7. PRISMA Control Maturity Model Overview |
|
|
8. Results by Control Reference |
For HITRUST i1 reports, Section 8 contains the results of all control references included in all HITRUST i1 assessments rather than the 75 controls required for HITRUST r2 Certification. |
|
9. Results by Assessment Domain |
No Differences |
|
Appendix A – Corrective Action Plans Required for Certification |
No Differences |
|
Appendix B – Additional Gaps Identified |
No Differences |
|
Appendix C – Assessment Results |
No Differences |
*Various sections noted above may include minor wording changes in order to differentiate between the HITRUST Risk-based, 2-year r2 Validated Assessment and the HITRUST Implemented, 1-year i1 Validated Assessment.
Additional resources
For an example of the HITRUST Implemented, 1-year (i1) Certification Report click here and for an example of the HITRUST Risk-based, 2-year (r2) Certification Report click here.
For any additional questions, please contact our Support team or a HITRUST Customer Success Manager.