Overview
The HITRUST CSF version 11 (v11) enables a fully traversable portfolio, which facilitates seamless movement between HITRUST assessments based on the use of common requirement statements to maximize reusability. As risk and compliance program maturity or information protection needs change, v11 allows organizations to use what they have already done to easily upgrade to higher levels of HITRUST assurance with just incremental effort. v11 enables cyber threat adaptive HITRUST Assessments across the portfolio that continuously evolve to address emerging threats such as ransomware and phishing.
The HITRUST CSF v11 framework includes new and refreshed Authoritative Sources powered by the speed and efficiency of Artificial Intelligence (AI). Plus, changes to Evaluative Elements and Illustrative Procedures that make it easier for MyCSF users to parse and score Requirement Statements.
Traversable and Threat-Adaptive Portfolio
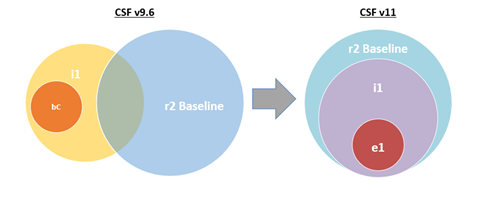
For v11, HITRUST has aligned the selection of requirement statements used for the e1 assessment (HAA 2023-004), i1 assessment, and r2 assessment baseline so that each assessment builds upon the core requirement statements that are included in the e1 assessment.
- The e1 assessment includes a selection of 44 requirement statements that address a curated set of cybersecurity controls generally viewed as fundamental essential cybersecurity practices, or “essential cybersecurity hygiene”.
- The i1 assessment includes a selection of 182 requirement statements that are comprised of the 44 e1 requirement statements along with an additional 138 requirement statements that address cybersecurity best practices and a broader range of active cyber threats than the e1 assessment.
- The r2 assessment includes the 182 i1 requirement statements as a baseline along with additional requirement statements that are included through the r2 assessment tailoring process.
This nesting of requirement statements allows organizations to begin with the entry-level e1 or moderate level i1 assessment and subsequently move through the assessment portfolio to demonstrate increased levels of information protection assurance without losing the investment made by completing previous assessments.
Threat-Adaptive Portfolio
As described in HAA 2021-012 and HAA 2023-004, e1 and i1 assessments are designed to be threat-adaptive through the selection of requirement statements that address active cyber security threats based on HITRUST’s quarterly reconciliation of cyber threat intelligence to the HITRUST CSF requirements. The inclusion of the i1 requirement statements in the r2 assessment introduces the threat-adaptive nature of the e1 and i1 to the r2.
Inheritance
External Inheritance can be used between v11 assessments and v9.1 – v9.6.2 assessments. However, due to the change in the r2 baseline described above, there may be requirement statements present in baseline v9.x assessments that are not present in baseline v11 assessments and vice versa. To address this, a Community Supplemental Requirement (CSR) and associated factor called “Legacy Inheritance Support” will be introduced for use in v11 assessments. The Legacy Inheritance Support factor includes additional inheritable 9.x requirement statements into v11 r2 Assessments. For additional information regarding the functionality and limitations of this factor, please see v11 FAQs.
HITRUST encourages inheritance providers using v11 to include the Legacy Inheritance Support factor so that their v11 r2 Assessment includes v9.x requirement statements that Assessed Entities may hope to inherit.
New and Refreshed Authoritative Sources
The Authoritative Source updates in v11 are powered by new AI processing technologies that enhance the efficiency of producing Authoritative Source mappings.
v11 contains the following new and refreshed Authoritative Sources:
- Added NIST SP 800-53 revision 5 mapping and selectable Compliance factor.
- Added Health Industry Cybersecurity Practices mapping and selectable Compliance factor.
- Refreshed NIST SP 800-171 mapping.
- Refreshed NIST Cybersecurity Framework mapping.
- Refreshed HIPAA Security Rule, Privacy Rule, and Breach Notification mapping.
Evaluative Elements Moved to the Requirement Statement
For assessments using v11, HITRUST has moved the evaluative elements from the policy level illustrative procedure to the requirement statement for improved visibility. Further, the requirement statement text is formatted to display each evaluative element in a numbered list.
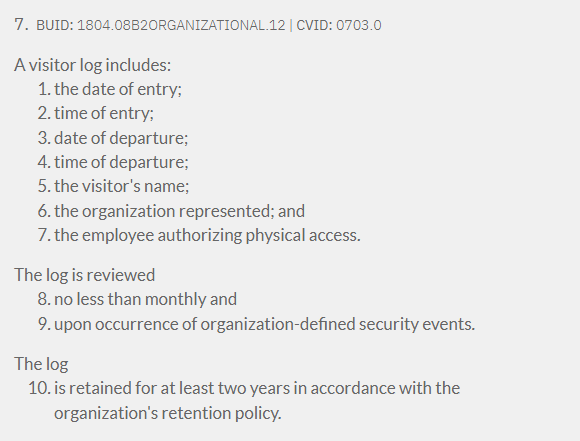
v11 Requirement Statement Example
For v9.1 – v9.6, the evaluative elements remain within the policy level illustrative procedures. Like v9.6, the illustrative procedure for v9.1 – v9.5 are now formatted to specifically enumerate each evaluative element as described in HAA 2021-014.
Illustrative Procedure Updates
Due to the move of the evaluative elements from the policy level illustrative procedure into the requirement statement, the v11 policy level illustrative procedures have been updated to standard text for all requirement statements. Additionally, the formatting of the v11 implemented and measured illustrative procedures have been updated to display the requirement specific implementation and measured testing guidance more clearly.
Clarification of Factor Definitions
HITRUST has updated the factor definitions to improve tailoring for v11 r2 assessments. Within MyCSF, the Factors page for r2 assessments using v11 will contain information icons that display the factor definition for reference.
The legacy factor definitions found at help.mycsf.net/factors should continue to be used for v9.1 – v9.6 r2 assessments.
Implementation and Timeline
v11 is available within MyCSF and for download here as of January 18, 2023.
Additional Information
In addition to the updates detailed above, CSF v11 includes assorted errata updates consistent with the CSF Versioning Policy. The errata updates include refreshes to BUIDs primarily based on changes to requirement statement levels and control references. Further, the following seven Authoritative Sources have been removed in CSF v11:
- CAQH CORE Phase 1 [CAQH Core Phase 1]
- CAQH CORE Phase 2 [CAQH Core Phase 2]
- Cloud Security Alliance (CSA) Cloud Controls Matrix Version 3.0.1 [CSA CCM v3.0.1]
- Department of Defense (DoD) Cybersecurity Maturity Model Certification (CMMC) version 1.0 [CMMC v1.0]
- Department of Homeland Security (DHS) Critical Resilience Review (CRR) v1.1 [DHS CISA CRR (2016)]
- ISO/IEC 29151:2017: Information Technology – Security Techniques – Code of Practice for Personally Identifiable Information Protection [ISO/IEC 29151:2017]
- Precision Medicine Initiative Data Security Policy Principles and Framework v1.0 (PMI DSP): Achieving the Principles through a Precision Medicine Initiative Data Security Policy Framework [PMI DSP Framework]
The CSF Summary of Changes document offers additional details regarding CSF changes. MyCSF subscribers can utilize the preview functionality described in HAA 2021-006 to determine impact on an existing assessment prior to upgrading to v11 including a detailed look at the direct changes that will apply to the assessment.
For a list of anticipated questions please click here.
For a comparison of the v9.6 i1 requirement statements to the v11.0 i1 requirement statements click here.
For any additional questions, please contact our Support team or a HITRUST Customer Success Manager.