By Tom Glaser, Practice Lead and Security Assessor, RSI Security
“Why did we ask the IT security auditor to cross the road? … Because that's the way we did it last year!”
 While the above is meant to be a joke, in all seriousness, organizations can no longer keep doing what they’ve always done when it comes to information security assurances. The game has changed to the point where it’s time to look at IT security as a competitive differentiator. If your IT organization is searching for a new way to conduct security assurances, as you evaluate options it’s critical to look at the value that various security frameworks provide to help strengthen your security posture and demonstrate information security program maturity.
While the above is meant to be a joke, in all seriousness, organizations can no longer keep doing what they’ve always done when it comes to information security assurances. The game has changed to the point where it’s time to look at IT security as a competitive differentiator. If your IT organization is searching for a new way to conduct security assurances, as you evaluate options it’s critical to look at the value that various security frameworks provide to help strengthen your security posture and demonstrate information security program maturity.
The value of the framework you choose comes down to determining your Return on Investment. Many organizations have discovered that the value generated by the HITRUST CSF surpasses what other frameworks can deliver. In this blog, we examine the value of a HITRUST Certification to validate how well your security program protects sensitive data.
The Value of HITRUST
In response to the increasing challenges of validating security posture, the HITRUST CSF framework is designed to be an assess-once process that addresses the requirements of a wide variety of major security frameworks. While HITRUST may require a greater up-front investment than other frameworks, it addresses multiple compliance requirements making the investment well worth it.
My Key Takeaway Regarding HITRUST: If there is one thing that HITRUST does better than other options, it’s the ability to accelerate through discussions with customers and stakeholders around data security assurances and managing risk. HITRUST brings a level of rigor with a certification that carries a strong reputation. That means when answering information protection inquiries, you can provide the short answer: “We're HITRUST Certified!”
Being HITRUST Certified is extremely beneficial because it allows:
- Your sales team to quickly address the security concerns of prospective customers.
- Your IT and risk management teams can enter into meaningful discussions with executives and other stakeholders regarding your organization's risk appetite and what is being done to address concerns.
Building Your Organization’s Internal and External ROI from a HITRUST Certification
By starting the HITRUST process, you generate an immediate return on your investment—even before you achieve full validation.
- Efficiently Meets Assurance Needs. The first and foremost benefit of HITRUST is your ability to accelerate through discussing and meeting data security assurance concerns as you share information and perform data-related services for business partners.
- Single Benchmark. Depending on the assessment and scope performed, the HITRUST CSF framework covers more than 40 authoritative sources – so one certification report may cover multiple needs.
- Competitive Advantage: HITRUST Certifications are widely adopted and recognized so they strengthen existing business relationships and help earn new partnerships.
- Save Time and Money. Many business partners require extensive InfoSec questionnaires that are expensive to complete and must be done individually – proactively offering a HITRUST Certification often bypasses or significantly reduces the number of onboarding questions.
- Internally Raises Security Posture. The HITRUST Approach identifies fundamental issues your organization can address to significantly improve cybersecurity effectiveness and reduce residual risk.
- Builds External Stakeholder Confidence. Uses proven, consistent, formalized processes to increase trust and transparency.
- Strong Negotiating Tool. Helps close contracts when you show that your organization is in the process of implementing HITRUST or has achieved certification.
- Cybersecurity Insurance Savings. Provides a strong proof point when renewing your policy.
- Actively Managed. The HITRUST Approach uses dedicated staff to update and revise controls in the CSF framework to meet the latest risk factors, security threats, and regulatory requirements. It offers a significant advantage compared to other frameworks such as PCI, which is managed on a limited scope or NIST, which is an excellent framework, but it is not actively managed.
Evaluating Your Resource Costs
NOW THAT YOU KNOW THE VALUE OF A HITRUST CERTIFIICATION, let’s address the other side of the ROI equation, which looks at the required investment. Internally, you will need to draw resources from across your organization, including IT staff, compliance and risk management teams, and a person to coordinate the assessment project. Depending on the maturity of your existing program, expect your resource team to put in 20-30 hours per week for up to 2-3 months.
External costs are also a factor, including an outside assessor firm to guide you through the process. In addition, while the HITRUST CSF framework is available for qualifying organizations to download at NO CHARGE, you will need to purchase a HITRUST MyCSF SaaS subscription for processing and reporting, along with a validated assessment credit from HITRUST.
Other direct and indirect costs include the additional tools you may need to meet the standards your security controls will be evaluated against during HITRUST Certification. In many cases, remediation work and additional budget allocation may be required to address identified gaps.
While total costs vary for each organization, there is no doubt that pursuing HITRUST Certification requires a commitment. However, the short-term and long-term benefits of improving information security and satisfying customer assurance requests more than outweigh the costs.
Multiple HITRUST Assessments Increase Efficiency with a Progressive Approach
HITRUST offerings include the Basic Current-state (bC) Self-Assessment, the Implemented 1-Year (i1) Validated Assessment, and the Risk-based 2-Year (r2) Validated Assessment. While the bC does not offer a certification, it does provide a strong starting point for implementing HITRUST and buys time for an organization to let stakeholders know they are working towards certification. The i1 provides a good balance of effort and level of assurance for any organization that wants certification, but is not prepared, or does not need, to go through a the more extensive r2 Assessment. The r2 provides the highest level of assurance for situations with greater risk exposure due to data volumes, regulatory compliance, or other risk factors. Both i1 and r2 offer Readiness Assessments that allow your assessor to help you evaluate your security controls against HITRUST criteria to understand program strength and which gaps you need to remediate.
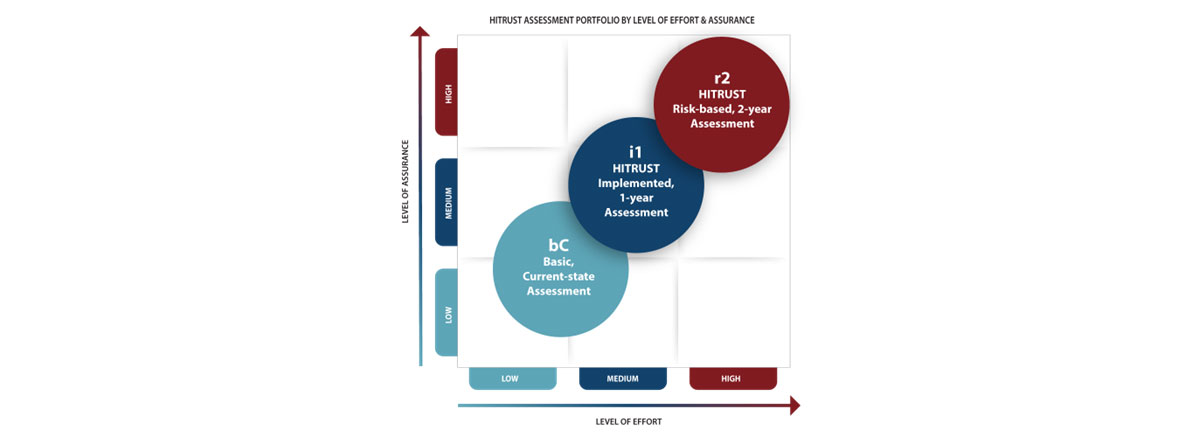
To Learn More and Compare the HITRUST Assessment Portfolio.
By using the right HITRUST Assessment along with the CSF framework and the HITRUST Approach, you’re proactively showing how seriously your organization takes information security while addressing information protection across your entire ecosystem. At the same time, you’re creating peace of mind for yourself and internal stakeholders that the organization is doing everything to protect sensitive digital assets. With everyone on edge about the possibility of a data breach and the significant consequences, that’s a priceless Return on Investment!
To get started with HITRUST, eligible organizations are invited to download the HITRUST CSF Free of Charge.
Follow HITRUST on X.
Follow HITRUST on LinkedIn.
About the Author
 Tom Glaser, Security Assessor and Auditor, RSI Security
Tom Glaser, Security Assessor and Auditor, RSI Security
Tom Glaser is Practice Lead and Security Assessor for RSI Security, a trusted advisor firm dedicated to helping organizations achieve cybersecurity risk-management success. Tom has been a technical consultant and information security professional for over 20 years—specializing in compliance and risk analysis. Tom is a member of ISACA and is an expert on a range of common security frameworks, including HITRUST, NIST, ISO 27002, PCI DSS, CIS CSE, HIPAA, and more. His professional certifications include CISA, CISM, HITRUST, PCI, and PMP.